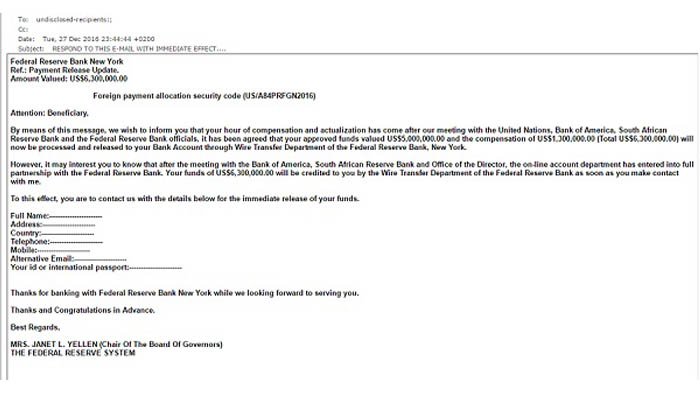
Because we are a high risk payment processor, we’re seeing an increase in phishing attacks by e-mail. Fortunately for us, each attack has been obvious, bordering on pathetic even. They’ve even given us a good laugh.
We’re lucky, however. Because of what we do, we can spot the red flags of fraudsters and unsavory millennials on the other side of the world who are up to no good. We consider ourselves pretty cyber savvy, and we’ve partnered with a tremendous IT company.
Not everyone recognizes phishing e-mails, however.
3 Examples of Failed Phishing Attacks
Somewhere there must be a gallery of screenshots of the ultimate phishing failures. We’ve received two in the last week to add to it. The third, however, looked legitimate.
- The first came from a representative of TrustSpay (sic), which is actually a reputable payment gateway based in Europe. This one sounded like a neutering service for pets. The message was replete with typos, an awful logo and text that would make an English teacher cringe – three dead giveaways of phishing attacks.
- The second attempt came from banking giant First Data, with the following message: ‘Because we registrated (sic) to many frauds we regret to inform you that your FirstData account has been locked. To re-activate it please download the file attached to this e-mail and update your login information.’
Not only is the message rife with typos, it was a one-line message with no name or logo, only signed ‘the FirstData (sic) team.’ And no one here has an account with First Data.
- More recently, we saw an example of a forged delivery form from Amazon, indicating there was a package waiting for a customer, but the customer needed to provide information on said form for delivery. It was a half decent attempt at a forgery, but there were several red flags:
- First, Amazon would never use this method of soliciting information.
- There was no contact phone number or e-mail on the form.
- Several terms that should’ve been capitalized, like the recipient’s name, strangely were not.
Do. Not. Click.
Simply, clicking the attachment on a questionable e-mail all but opens the door to your network and every piece of information on it.
When in doubt, here are some things to know and ask:
1. Who is contacting me and why?
With every e-mail received with an attachment, it is a vitally important question. If you’re real curious, it might be worth a phone call to the sender to find out what the attachment exactly contains.
2. What are some other red flags of phishing e-mails?
Typos, fragments and run-on sentences soliciting information should evoke suspicion. So should weak replicas of company logos – or no logo at all.
3. What do I do with this e-mail?
File it in your spam or quarantine folder. This way, your e-mail server will be alerted next time a message comes from this sender.
Have You Experienced Phishing Attacks?
We are interested to read your phishing stories.
Has the royal family of a country on the other side of the world contacted you?
Did you win the lottery in Burma?
Share your stories in our comment box below.